
Industrial-Strength Design Thinking for cybersecurity.
To make cyber as reliable as electricity and cyber careers more rewarding.
Innovation, design, education and acceleration

Cyber pros need to respond to increasing incidents and costs
- Forensic and root cause analysis reveal most breaches are self-inflicted.
- Caused by structural flaws wrongly designed into cybersecurity methods.
- Thus, cyber pros are set up to fail and wastes resources.
- There is a better way.
- Proven and practical methods create better work life and safer world for us all.

What questions do you most need to answer?
- What is symptom and what is root cause?
- Why is danger increasing, including to personal safety?
- Why is improvement so difficult, especially organizationally?
- Why are cyber pros burned out?
- Why is cyber left behind compared to innovation and learning in other disciplines?
What most hurts your progress?
- Rising threats & attacks
- Rising cost of people and tech
- Uncertain outcomes
More...
- Silos within "the business," IT and cyber
- Mistrust and infighting across silos and people
- Constrained resources
- 5000+ point products, "expense in depth"
- Hamster wheel futility
- "Group think" conformity to fuzzy "standards"
- People stress and burnout
- Work-life conflict


Consider... are the above symptoms or root causes?
Symptoms.
What does forensic systems and root cause analysis reveal?
Cyber math and methods are structurally flawed due to errors that are designed into "standard" methods. It is like a structural flaw in an apartment building that was caused by a design error. Fancy decor cannot fix the structural danger.
Structural flaws flow from faulty assumptions.
For example, which is correct about the nature of the system in which cyber risk lives?
- Linear, stable system, highly-rules based, where most of bad actors are internal
- Complex, dynamic, often chaotic and highly adversarial where most bad actors are external
False assumptions lead to errors in math and method, data and measurement, and selection and use of point products -- leaving "expense in depth."
Method errors hurt cyber pros -- causing stress and work-life damage.
Cyber is a "wicked problem" (as described by Rittel and Webber).
More tech point products cannot solve the real problem in the real system.
Cyber pros need something more, especially...
When your needs are to...
- Implement stronger strategies -- authentic Zero Trust
- Accomplish business objectives
- Cut wasteful costs and boost efficiency
- Avoid incidents
- Influence organization dynamics
- Attract top talent
- Give your team, your family and yourself wins
- Achieve work-life balance
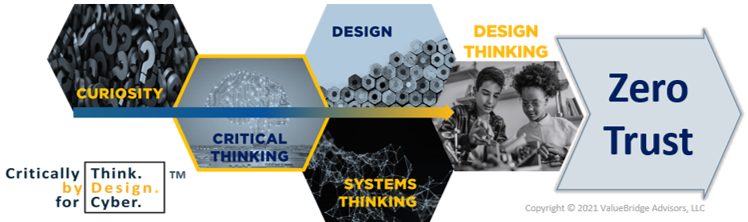
By
- alizing system reality
- Fixing structural flaws at root cause
- Redefining how we work
- Implementing authentic Zero Trust

Your needs
are our mission at
Think.Design.Cyber
Industrial-Strength Design Thinking
- Pioneering cyber-domain specific coaching for people and leaders of diverse high-performing teams
- Outcomes Accelerator Workshops for 6 months of work in 6 weeks
- Solution hack-a-thons
For cyber pros:
- Better work-life balance
- Better protect people from danger
- Putting people in the center of cybersecurity
Contact us for a consult to learn more
© Copyright 2010-2023. All rights reserved. ValueBridgeAdvisors, LLC
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details and accept the service to view the translations.